Support models:
ES3510MA, ES3528MV2, ECS3510-28T/52T, ECS4110 series, ECS4510 series, ECS4620 series
Scenario: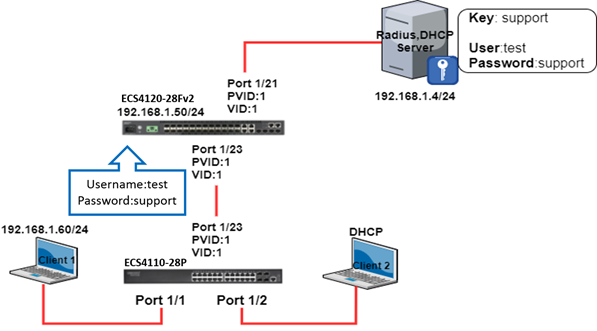
When devices attached to a port, the port must submit requests to another authenticator on the network; however, the end clients do not support 802.1x authentication or prevent untrust device, neither the non-support supplicant device connection to the network. The user could configure the identity profile parameters to identify this switch as a supplicant, and enable dot1x supplicant mode for those ports which must authenticate clients through a remote authenticator.
Test procedures:
Step 1) Configure the management IP address
ECS4120-28Fv2:
ECS412028Fv2#configure
ECS412028Fv2(config)#interface vlan 1
ECS412028Fv2(config-if)#ip address 192.168.1.50/24
Step 2) Define an external RADIUS server
ECS4120-28Fv2:
ECS412028Fv2#configure
ECS412028Fv2(config)#radius-server 1 host 192.168.1.4 key support
Step 3) Check the configuration of RADIUS
ECS412028Fv2#show radius-server
Remote RADIUS Server Configuration:
Server 1:
Server IP Address: 192.168.1.4
Authentication Port Number : 1812
Accounting Port Number : 1813
Retransmit Times : 2
Request Timeout : 5
Step 4) Enable 802.1x port authentication globally on ECS4120-28Fv2
ECS4120-28Fv2:
ECS412028Fv2#configure
ECS412028Fv2(config)#dot1x system-auth-control
Step 5) Configure 802.1x mode on switch port
ECS4120-28Fv2:
ECS412028Fv2#configure
ECS412028Fv2(config)#interface ethernet 1/23
ECS412028Fv2(config-if)#dot1x port-control auto
Step 6) Allow multiple hosts connect to the same switch port
ECS4120-28Fv2:
ECS412028Fv2#configure
ECS412028Fv2(config)#interface ethernet 1/23
ECS412028Fv2(config-if)#dot1x operation-mode multi-host
Step 7) Check the 802.1x configuration status is correct
ECS4120-28Fv2:
ECS412028Fv2#show dot1x
Global 802.1X Parameters:
System Auth Control : Enabled
Authenticator Parameters:
EAPOL Pass Through : Disabled
802.1X Port Summary
Port Type Operation Mode Control Mode Authorized
-------- ------------- -------------- ------------------ ---------
Eth 1/21 Disabled Single-Host Force-Authorized Yes
Eth 1/22 Disabled Single-Host Force-Authorized N/A
Eth 1/23 Authenticator Multi-Host Auto N/A
Eth 1/24 Disabled Single-Host Force-Authorized N/A
Eth 1/25 Disabled Single-Host Force-Authorized N/A
Eth 1/26 Disabled Single-Host Force-Authorized N/A
Step 8) Try to ping the radius server from Client1
Client 1 : Ping failed because the port was not authenticated by RADIUS server.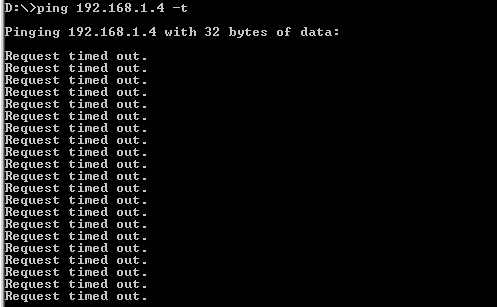
Step 9) Check the version on ECS4110-28P which support dot1x supplicant mode
ECS4110-28P(DUT):
Dut1#show version
Unit 1
Serial Number : EC1427000158
Hardware Version : R0A
EPLD Version : 0.00
Number of Ports : 28
Main Power Status : Up
Role : Master
Loader Version : 1.2.0.1
Linux Kernel Version : 2.6.22.18
Boot ROM Version : 0.0.0.1
Operation Code Version : 1.2.3.13
Step 10) Enable dot1x supplicant mode on port interface
ECS4110-28P(DUT):
Dut1#configure
Dut1(config)#interface ethernet 1/23
Dut1(config-if)#dot1x pae supplicant
Step 11) Set up the dot1x supplicant Username and Password
ECS4110-28P(DUT):
Dut1#configure
Dut1(config)#dot1x identity profile username test
Dut1(config)#dot1x identity profile password support
Step 12) Reconnect the port 1/23 of ECS4110-28P to re-authenticate.
ECS4110-28P(DUT):
Dut1#configure
Dut1(config)#interface ethernet 1/23
Dut1(config-if)#shutdown
Dut1(config-if)#no shutdown
Step 13) Check the status of dot1x on ECS4120-28Fv2
ECS4120-28Fv2:
ECS412028Fv2#show dot1x interface ethernet 1/23
802.1X Authenticator is enabled on port 1/23
Reauthentication : Disabled
Reauth Period : 3600 seconds
Quiet Period : 60 seconds
TX Period : 30 seconds
Supplicant Timeout : 30 seconds
Server Timeout : 10 seconds
Reauth Max Retries : 2
Max Request : 2
Operation Mode : Multi-Host
Port Control : Auto
Maximum MAC Count : 5
Intrusion Action : Block traffic
Supplicant : 70-72-CF-C8-58-8F // ECS4110-28P(DUT)’s MAC Address
Authenticator PAE State Machine
State : Authenticated
Reauth Count : 0
Current Identifier : 1
ECS4110-28P(DUT):
Dut1#show dot1x
Global 802.1X Parameters:
System Auth Control : Disabled
Authenticator Parameters:
EAPOL Pass Through : Disabled
Supplicant Parameters:
Identity Profile Username : test
802.1X Port Summary
Port Type Operation Mode Control Mode Authorized
-------- ------------- -------------- ------------------ ----------
Eth 1/22 Disabled Single-Host Force-Authorized N/A
Eth 1/23 Supplicant Single-Host Force-Authorized Yes
Eth 1/24 Disabled Single-Host Force-Authorized N/A
Eth 1/25 Disabled Single-Host Force-Authorized N/A
802.1X Port Details
802.1X Authenticator is disabled on port 1/23
802.1X Supplicant is enabled on port 1/23
Authenticated : Yes
Auth-period : 30 seconds
Held-period : 60 seconds
Start-period : 30 seconds
Max-start : 3
Step 14) Retrieve the packet by wireshark on RADIUS Server
Authentication Successfully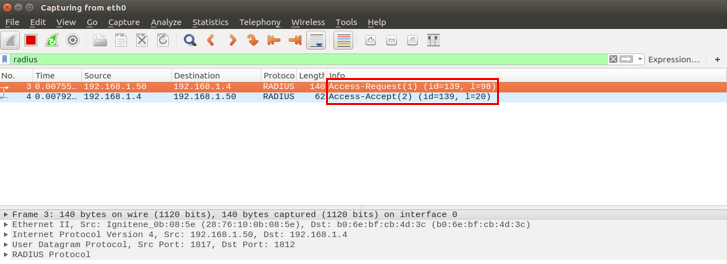
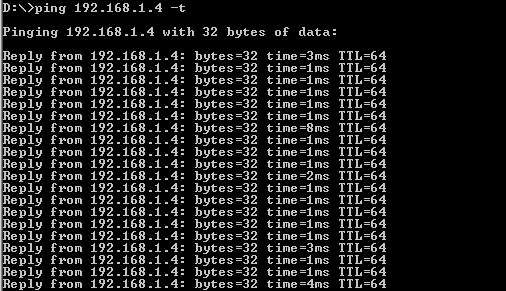
Step 15) Try to ping the radius server again from Client1
Client 1 : Ping Successfully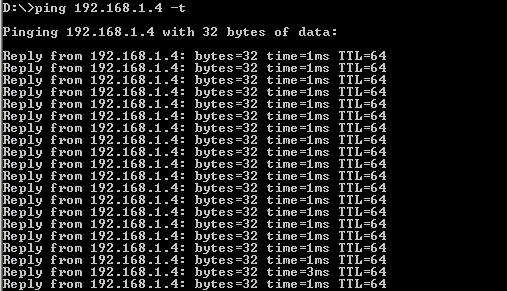
Client 2 : Successfully obtain the IP address by DHCP Server and ping to radius server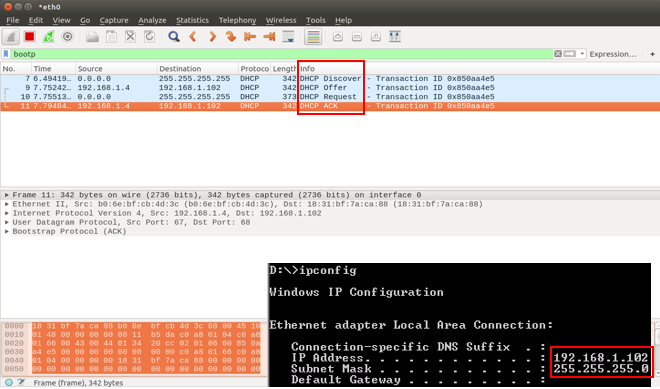
Prev Page How to add/delete the IPv4 and IPv6 static route entry via SNMP?
Next Page Unable to access Edgecore switch(EdgeCOS) via SSH?
