Topology:

Step:
1. Setup FreeRadius Server
2. Configure client
3. Configure switch
4. Verify
1. Setup FreeRadius Server
<1> Install freeradius server to Ubuntu(Ubuntu 14.04) as follow command:
FreeRadius ~ # apt-get install freeradius -y
<2> Configure "users" and "clients.conf" file
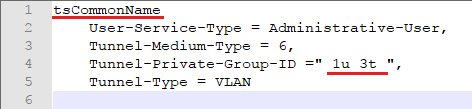
Users (path: /etc/freeradius/users)
Username "tsCommonName". It must be as same as commonName in the client.cnf (refer to step <4>)
"Tunnel-Private-Group-ID" parameter is for dynamically adding VLAN
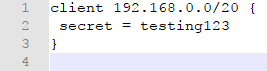
Clients.conf (path: /etc/freeradius/clients.conf)
<3> Download the FreeRadius source code from https://freeradius.org/
FreeRadius ~ # wget ftp://ftp.freeradius.org/pub/freeradius/freeradius-server-3.0.15.tar.gz
After decompress the source file, use files "~/freeradius-server-3.0.15/raddb/certs" to replace "/etc/freeradius/certs"
Reference commands:
FreeRadius certs # pwd /etc/freeradius/certs FreeRadius certs # rm -rf * FreeRadius certs # cp -Rf ~/freeradius-server-3.0.15/raddb/certs/* .
<4> Modify ca files: server.cnf / client.cnf
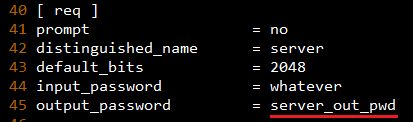
server.cnf: modify output_password (path: /etc/freeradius/certs/server.cnf)
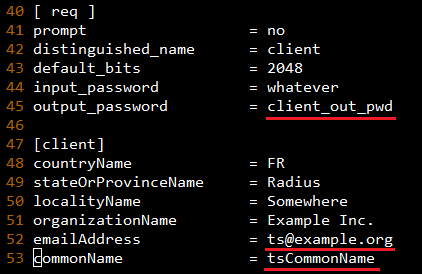
client.cnf: modify output_password, emailAddress and commonName
(path: /etc/freeradius/certs/client.cnf)
commonName need same as "Username" in users file
<5> Launch bootstrap script (path: /etc/freeradius/certs/bootstrap)
FreeRadius certs # ./bootstrap
<6> Copy "ca.pem", "client.key" and "ts@example.org.pem" (which is as same as "emailAddress" parameter) to Client.
Path:
/etc/freeradius/certs/ca.pem
/etc/freeradius/certs/client.key
/etc/freeradius/certs/ts@example.org.pem
<7> Modify eap.conf file (path: /etc/freeradius/eap.conf)
a. Change default_eap_type to tls
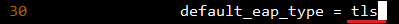
b. Remove(delete or comment) the make_cert_command
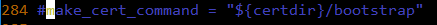
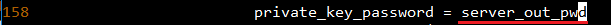
c. Change "private_key_password" value as same as server.cnf's output_password.
<8> After all Server side configuration is finished, restart the FreeRadius server.
You can use command:
a. start server normally or
FreeRadius freeradius # Service freeradius start
b. start server with debug mode
FreeRadius freeradius # Freeradius -X
2. Configure client
<1> Get the three files at configure server, please refer to "Setup FreeRadius Server" step <6>.
"ca.pem", "client.key" and "ts@example.org.pem" (which is same as "emailAddress" parameter)
<2> Add CA to client and update CA
Commands:
root@ts:/home/ts/Desktop# cp ca.pem /usr/local/share/ca-certificates/ca.pem.crt root@ts:/home/ts/Desktop# update-ca-certificates
<3> Configure Client's network configure
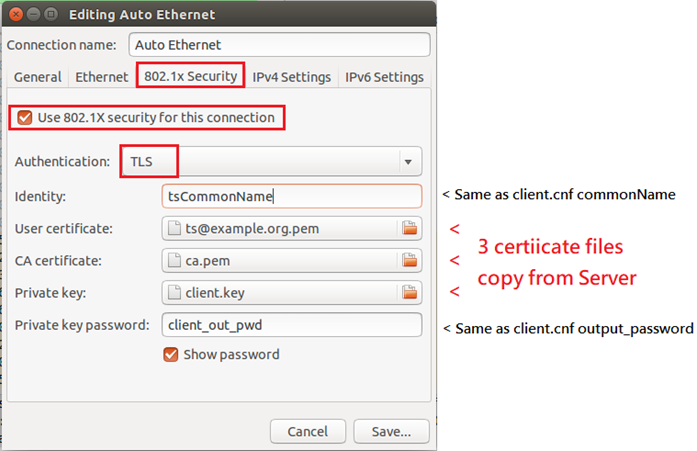
3. Configure switch
<1> Switch IP:
Console#configure Console(config)#interface vlan 1 Console(config-if)#ip address 192.168.2.46/20
<2> Switch VLAN:
Console(config)#vlan database Console(config-vlan)#vlan 3
<3> 802.1x configure:
Global Configuration:
Console(config)#dot1x system-auth-control
Interface Configuration:
Console(config)#interface eth 1/3 Console(config-if)#dot1x port-control auto
4. Verify
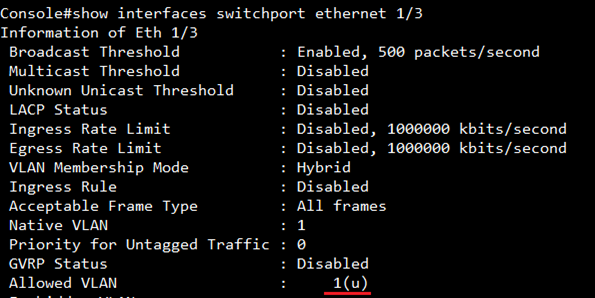
Before client authentication, port #3 only allows the traffic which belong to VLAN 1(u).
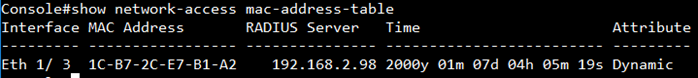
After authentication, port #3 allows the traffic which belong to VLAN 1(u) and 3(t).
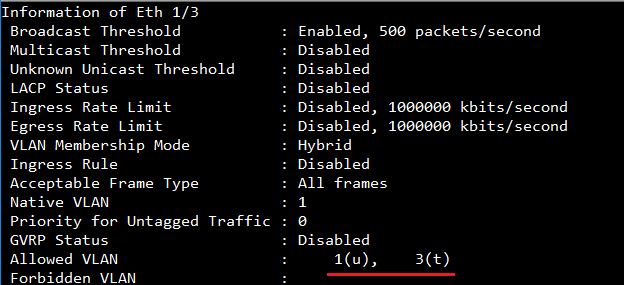
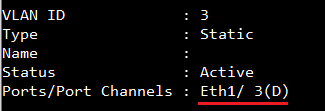
In show VLAN, you can see port #3 dynamic add to VLAN 3.
Next Page How to allow the user who belongs Level X to execute the command on Edgecore switch ?
