Models: ECS4620 series, ECS4510 series, ECS4120 series, ECS4110 series, ECS4100 series, ECS2100 series, ES3510MA
Introduction:
There are many AVP defined in TACACS+ draft show as below link,
https://tools.ietf.org/html/draft-grant-tacacs-02
Edgecore switch support only 3 AVP of them for TACACS+ authorization now:
1. service
2. shell
3. priv-lvl
About un-supported AVB, Edgecore switches consider the authorization to have failed.
Please refer to page No. 27 in the draft.
arg
An attribute-value pair that describes the command to be performed.
(see below)
The authorization arguments in both the REQUEST and the RESPONSE are
attribute-value pairs. The attribute and the value are in a single
ascii string and are separated by either a "=" (0X3D) or a "*"
(0X2A). The equals sign indicates a mandatory argument. The asterisk
indicates an optional one.
Optional arguments are ones that may be disregarded by either client
or daemon. Mandatory arguments require that the receiving side under-
stands the attribute and will act on it. If the client receives a
mandatory argument that it cannot oblige or does not understand, it
MUST consider the authorization to have failed. It is legal to send
an attribute-value pair with a NULL (zero length) value.
Attribute-value strings are not NULL terminated, rather their length
value indicates their end. The maximum length of an attribute-value
string is 255 characters. The following attributes are defined:
Problem:
Users may not obtain correct privilege level if they receive mandatory un-supported AVP from TACACS server.
Solution:
Change mandatory AVP to optional AVP on TACACS server.
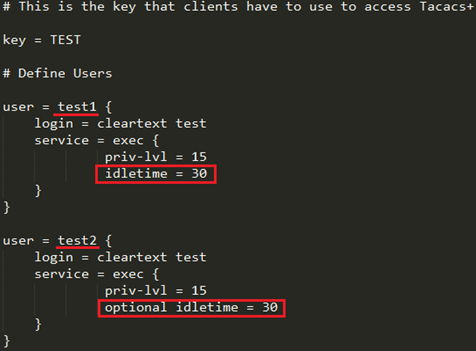
TACACS setting as shown below:
There are two users.
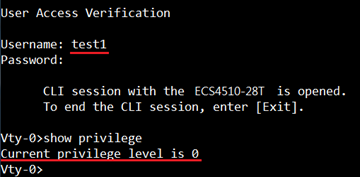
User test1 with mandatory AVP "idletime".
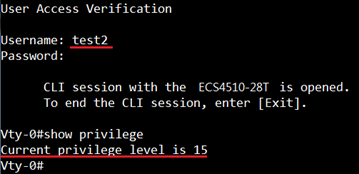
User test2 with optional AVP "idletime".
/etc/tacacs+/tac_plus.conf
User test1 obtain privilege 0.
User test2 obtain privilege level 15.
Prev Page Use RSPAN to mirror traffic from remote switches
Next Page How to configure VLAN (create/delete/add member ports) via SNMP ?
